Benefit from our experience
The Internet of Things (IoT) integrates cyber-physical systems that bring new functionalities, optimised operations and emerging business models. Yet, they also create new security risks on data protection and safety. If you are an IoT manufacturer, a service provider or a end-user in consumer IoT or Industrial IoT, we accompany your IoT security journey!
At cetome, we understand the challenges of IoT security and its complexity. We work with the entire IoT ecosystem to make products and systems more secure throughout their lifecycle
Comply with new regulations and certifications
We support our clients to comply with IoT cyber security regulations such as UK PSTI, EU RED and EU CRA.
You are an IoT manufacturer? We accompany you to enhance your cyber security and to review your compliance.
You are an IoT user? We develop appropriate requirements to better secure your supply-chain.
Access our panorama for more information.
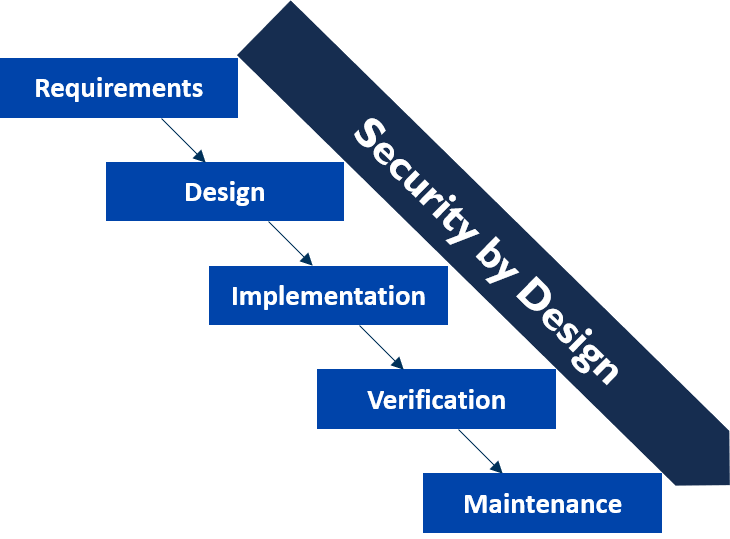
Embed security in the development process
IoT security requires securing every stage of the product lifecycle, from conception to release. Our experience allows us to integrate security by design requirements in your products and your processes.
Our innovation? We will collaborate with your teams to secure products that are already in development!
With us, product security is cheaper and faster. And if you want a better idea of our capabilities, you can try #FAST for free.
Keep products secure throughout their lifecycle
Building a secure product is the first step to ensure that they remain secure on the market. New regulations impose several requirements: providing support for given period, learning and fixing vulnerabilities, managing incidents, etc.
We will help you understand and implement these requirements and all pre-requisites (internal organisation, processes and tools)
With cetome, secure your products until their end of life with important mechanisms such an accessible vulnerability disclosure policy.
Develop IoT security skills
IoT systems are complex and combine expertise from multiple domains.
When developing or integrating IoT systems, cyber security demands a holistic approach.
Our expertise with manufacturers and end-users gives us an advantage to face IoT security challenges and cyber threats. We will help you comply with new standards and regulations. If you need more information we offer a discovery session on IoT cyber security standards and regulations as well as an in-depth training on EN 303 645.