Duration: 1 hour
Audience: Project managers, product owners, security experts new to IoT, developers, IoT manufacturers
Level: Easy
Price: This session is available in live sessions or as a package to deploy on your internal training platform
Contact Us to register your interest.
IoT systems are complex and are challenging to secure, knowing that a vulnerability can present a risk to safety and privacy.
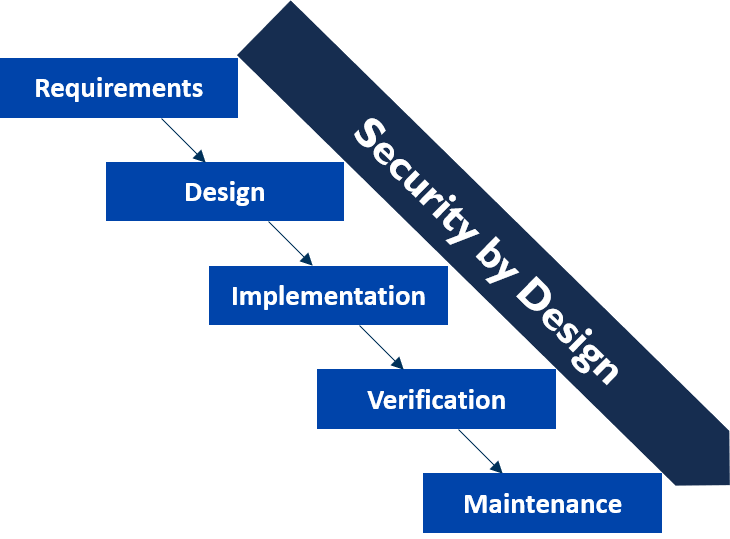
In this one-hour awareness session, participants will discover the differences between IoT and IT security, understand how cyber attacks can compromise IoT systems, and learn cyber security principles to protect IoT products at every stage of their lifecycle.
This course is ideal for non-technical participants such as project and product managers, new IoT manufacturers and startups, who want to learn the basis of IoT security. This training course is also built for developers and security experts who want to update their knowledge on IoT security.
Objectives:
- Understand the security challenges of IoT systems
- Get up to date with the latest security threats and vulnerabilities to IoT systems
- Learn about good security practices and how they apply to prevent cyber attacks
Programme:
- Introduction to IoT systems and their differences with IT systems
- The security challenges of IoT
- The threats to IoT systems and the risks on users, systems and the society
- Presentation of high-level cyber security concepts to secure IoT systems
Contact Us to receive a quote or register your interest.