Duration: 1 hour
Audience: Project managers, product owners, future IoT security experts, software developers, non-IoT security consultants, senior management
Level: Easy
Price: This session is available in live sessions or as a package to deploy on your internal training platform

How often can we see a new vulnerability with millions of IoT systems compromised, affecting our privacy and our safety? Too often! Why are we still seeing IoT products used in cyber attacks after all these years?
In most cases, product teams are NOT managing product cyber security after market release. This is now a regulatory requirement and urgent action is needed!
In this one-hour awareness session, you will discover how to protect IoT products after their release on the market. You will learn several concepts and tools to identify new cyber security issues and fix them in compliance with new cyber security regulations.
The goal of the course is to improve product cyber security post-release. For that purpose, we will explain how Software Bill of Materials (SBOM), vulnerability disclosure and management, and other important topics work together to fulfill this objective.
This session is available in live session or as a package that you can deploy on your internal training platform. The content remains accessible to non-security experts. There is no coding and no hacking involved.
Objectives:
- Understand the challenges of securing product after market release
- Know the different possibilities to secure products after release and how these concepts and tools work together
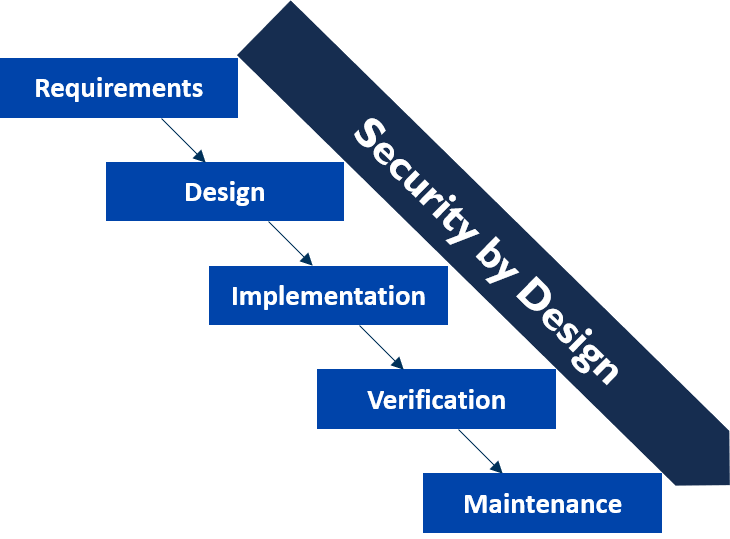
- Be able to plan these requirements in the product development phase
Programme:
- Introduction to product cyber security after market release
- The concepts and tools to secure products in the market
- How to combine these schemes to improve security throughout the product lifecycle
- Pre-requisites to integrate these requirements in the product development phase.