Duration: 1/2 to 1 day
Audience: Software developers, IoT manufacturers (product teams, engineering teams, developers), non-security technical subject matter experts
Level: Advanced
This training is tailored to your internal processes!
Contact Us to receive a quote or register your interest.
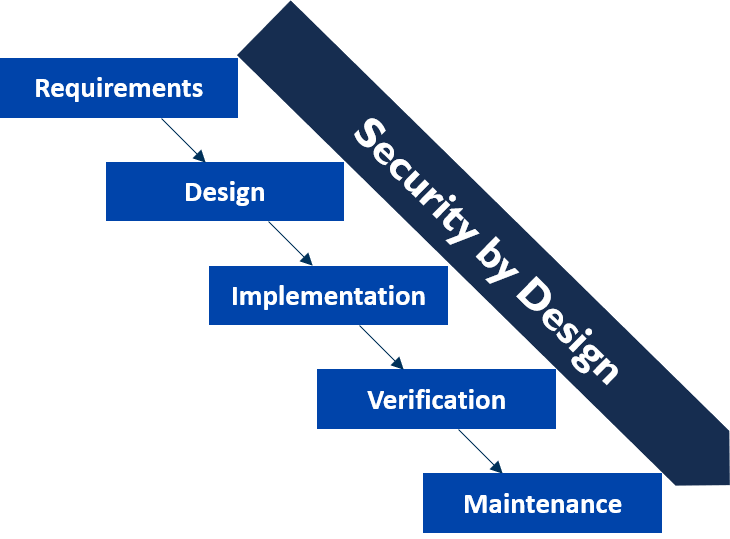
The principle of Security by Design integrates security at the early stages of a project to make it more efficient and effective.
In this 1/2-day training course, we learn how to embedded security into the existing processes at every stage of a solution's lifecycle: from its conception, its deployment and operation, and until its end of life. You will learn to about the requirements at the early stages of a project, and discover how to use security assurance mechanisms throughout the development process. For every stage, you will be able to identify roles, responsibilities and accountabilities around security.
This training course is ideal for software developers, IoT manufacturers (product teams, engineering teams, developers), and non-security technical subject matter experts.
You will study a real-life example where security by design helped an IoT manufacturer save several millions of pounds while developing an IoT system that integrates third-parties with various technologies (devices, mobile apps and Cloud). This training course is also built for security technical experts who want to extend their knowledge or support project and product development.
Objectives:
- Understand the issues around the current security status
- Understand the principles of security by design
- Understand the benefits of a security by default approach
- Be able to define security requirements at project start
- Understand the importance of coordination and communication around security functions
- Manage security throughout the product development
Programme:
- Presentation of several high-profile cases of attacks against IoT systems.
- Explain how the lack of “security by design” led to vulnerabilities affecting a product and the reputation of a company
- Define Security by Design and Security by Default
- How security usually integrates into the lifecycle of a project, including supply-chain security
- Managing security throughout product development
- Validation through security assurance
Contact Us to receive a quote or register your interest.