Tackle the cyber skill gap!
Security is an evolving topic: new threats, new standards, new regulations. Training brings an opportunity to stay on top of it.
At cetome, we believe anyone can increase their cyber security skills!
We make our courses accessible to everyone with an interest in security.
We designed our training material to make it enjoyable by all participants and ensure that all attendees gain benefits in their daily activities.
In all our courses, our exercises represent real-life scenarios to ally theory and practice. Our trainers remain accessible to foster discussion and share their experience.
We offer training courses in two domains:
IoT Security

Know how to secure IoT products with the EN 303 645 standard to be compliant with new regulations
- Audience: Software developers, product owners, product managers, IoT manufacturers, security consultants, security experts, auditors
- Duration: 2 days
- Level: Easy

Discover how standards and regulations are shaping IoT cyber security
- Audience: Project managers, product owners, future IoT security experts, software developers, non-IoT security consultants, senior management
- Duration: 1 hour
- Level: Easy
Better understand IoT cyber security risks
- Audience: Project and product managers, security experts new to IoT, developers, IoT manufacturers
- Duration: 1 hour
- Level: Easy
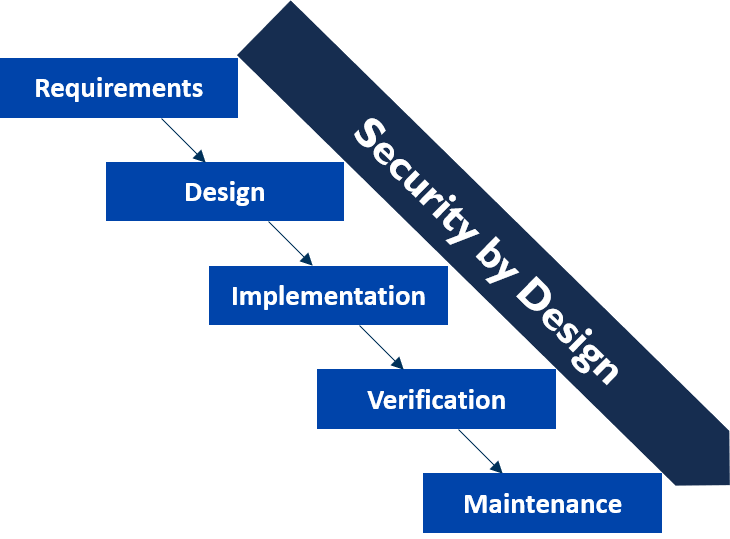
Secure IoT products throughout their lifecycle
- Audience: Software developers, IoT manufacturers (product teams, engineering teams, developers), non-security technical subject matter experts
- Duration: 1/2 to 1 day
- Level: Advanced

Identify and manage vulnerabilities in products to better protect your customers
- Audience: Product security teams, product owners, customer support teams, developers, IoT manufacturers
- Duration: 1 hour
- Level: Easy

The most important concept to secure IoT products
- Audience: Hardware engineers, Embedded developers, product security teams, IoT manufacturers
- Duration: 2 hours
- Level: Advanced
NIS Directive
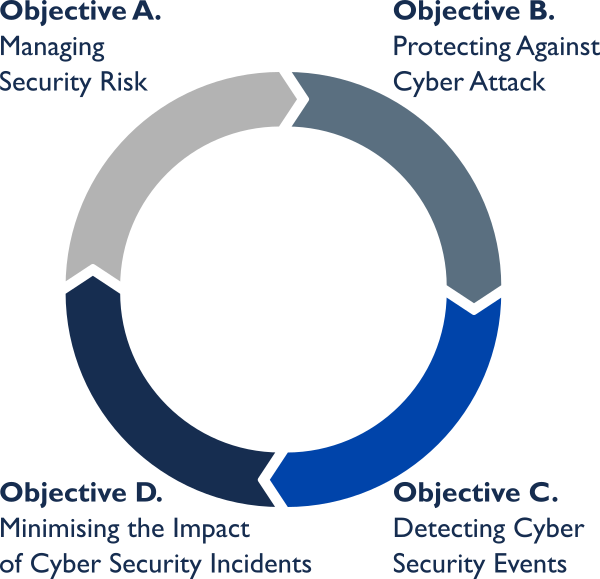
Achieve NIS Compliance with the Cyber Assessment Framework
- Audience: UK Operators of Essential Services, UK Competent Authorities, Head of OT, security managers, infrastructure managers, security consultants
- Duration: 3 days
- Level: Advanced







