The NIS Directive is a European Directive, which means it requires Member States to transpose it in their local law. In this article, we focus on the implementation of the NIS Directive in the United Kingdom: the “Network and Information Systems Regulations 2018” or “NIS Regulations”. We will present how the NIS Regulations defines roles and responsibilities in the UK, and how the approach is adapted to fit the local culture and existing regulatory environment.
This third article is part of a series that aims to better apprehend this directive. It follows an introduction on the NIS Directive and a second article on scoping the NIS Directive.
The NIS Regulations
The NIS Regulations entered in force the 10th of May 2018, which makes the UK one of the leading players in Europe (for instance, Belgium has voted their local implementation in March 2019).
The NIS Regulations defines:
- The roles and responsibilities to implement the NIS Directive in the UK
- The obligations of Operators of Essentials Services (OES) and Relevant Digital Service Providers (RDSP)
- Rules for enforcement and penalties
In this article, we explore the regulatory requirements for these three points.
Note: the NIS Regulation does not apply to Banking and Financial Market Infrastructures as equivalent EU legislation applies.
Roles and Responsibilities
This part is a simplified summary of the roles and responsibilities defined in the NIS Regulations. To know more about the legal roles and responsibilities of each stakeholder, please refer to the text of the NIS Regulations.
Operators of Essential Services
The NIS Regulations defines the sectors in scope for OESs, as well as the thresholds for the designation of these OESs. In the NIS Regulations, OESs in scope must rely on network and information systems to provide a service essential to the society.
The OESs must implement appropriate and proportionate security measures and notify their Competent Authority of any significant incident within 72 hours after discovery. This time-bound requirement aligns with the requirements of the GDPR/Data Protection Act 2018.
Relevant Digital Service Providers
The NIS Regulations defines Relevant Digital Service Providers (RDSPs) as DSPs with a headquarter or a representative in the UK. Micro and small enterprises are not in scope. The Information Commissioner’s Office (ICO), which acts as the Competent Authority, has clarified these requirements: RDSPs in scope must have over 50 staff and a turnover or balance sheet of more than 10 million Euros.
Note: when part of a larger organisation, DSPs must consider the whole organisation’s staff and turnover.
Similarly to OESs, RDSPs must implement appropriate and proportionate security measures to mitigate the security risks they face. They must also notify their Competent Authority of any significant incident within 72 hours after discovery.
Competent Authorities
The NIS Regulations defines Competent Authorities (CAs) for each sector, sub-sector, and sometimes per region (i.e. Nation State). In the UK, a few sectors have more than one CA. This choice is to capitalise on the existing regulatory environment and geographical particularities in the UK.
CAs have several regulatory responsibilities around the implementation and the application of the NIS Regulations in their sector and region. CAs designate OESs, define incident thresholds, receive notifications of NIS Incidents, and investigate these incidents.
CAs must also prepare and publish guidance to assist their OESs/DSPs in meeting the requirements of the NIS Regulations. They assess their compliance and have an enforcement role.
Since they have an overview of the security posture of their sector, CAs collaborate with their peers and other national bodies defined in the NIS Regulations. This is to improve the overall security posture in the UK.
Note: The list of competent authorities is available in Schedule 1 of the NIS Regulations.
Computer Security Incident Response Team (CSIRT)
In the NIS Regulations, the CSIRT provides a 24/7 support to OES and DSPs on “cyber” matters. As its name suggests, the CSIRT has an active role around security incidents. They monitor potential incidents, provide incident response and post-incident support.
When a NIS Incident occurs, the CSIRT can directly intervene to support an OES/RDSP in their incident response. For that purpose, OESs and RDSPs can directly request assistance from the CSIRT when suffering from a NIS Incident (after notifying their CA). The CSIRT can also inform other OESs/DSPs and the public of such incidents.
When an incident has a cross-border impact, the CSIRT coordinates the response with other affected Member States.
Moreover, the CSIRT contributes to enhancing the security preparedness at national level. It plays a central role in every aspect of cyber security by communicating on awareness, threat intelligence, risks, incidents, etc.
The National Cyber Security Center (NCSC) is the national CSIRT for every sector, except the healthcare sector where NHS Digital assumes this role.
Single point of contact (SPOC)
The SPOC has primarily a liaison role with other Member States. They facilitate cross-border cooperation and communication, by being the single point of contact for foreign CSIRTs.
Legally, the SPOC must also produce and submit annual incident reports to the NIS Cooperation Group (see below). For that purpose, the SPOC works at national level by collecting and analysing incident reports from Competent Authorities. This report can highlight trends and root causes, number of incidents per sector, etc. It can act as a benchmark to better measure the security posture per sector and at national level, and serve as a basis for future decisions (priorities, improvements, etc.)
On top of this annual report, the SPOC must also produce a biennial report identifying the number of OESs for each subsector. This could help assess the evolution of specific sector and the alignment of the national cyber security strategy.
In the UK, the NCSC is the Single Point of Contact.
Technical Authority
The NIS Regulations introduces a new stakeholder: the Technical Authority. Its role is to support both competent authorities in their regulatory function, and OESs/RDSPs to ensure they can implement the requirement of the NIS Regulations.
The Technical Authority works closely with competent authorities. It provides expertise and advice, and facilitates the exchange of best practices across sectors through working groups.
The NCSC is the Technical Authority. In order to fulfil their role, they develop and maintain several documents and guidance:
- The “NIS Security Principles” and the “NIS Guidance Collection”.
- The “Cyber Assessment Framework” (CAF) for compliance assessments by Competent Authorities.
Note: The technical authority is not defined legally in the NIS Regulation. This role and its responsibilities appear in the DCMS “NIS Guidance for Competent Authorities”, which explains how the NIS Regulations should apply in the UK.
The NIS Cooperation Group
The NIS Cooperation Group is an EU-wide group composed of representatives of Member States, the European Commission and ENISA. Its role is to foster strategic international cooperation at EU-level by supporting information exchange between Member States.
The Cooperation Group aims to leverage the experience of the NIS Directive in individual Member States to augment the global security posture at EU-level. It can decide improvements on national implementations, as well as on the text of the NIS Directive itself.
The Department for Digital, Culture, Media and Sport (DCMS) is the UK representative in the NIS Cooperation Group. It represents the interests of the UK CSIRT, SPOC and CAs and shares with them any guidance produced by the Cooperation Group.
Note: All UK interactions with the NIS cooperation group shall pass through the DCMS.
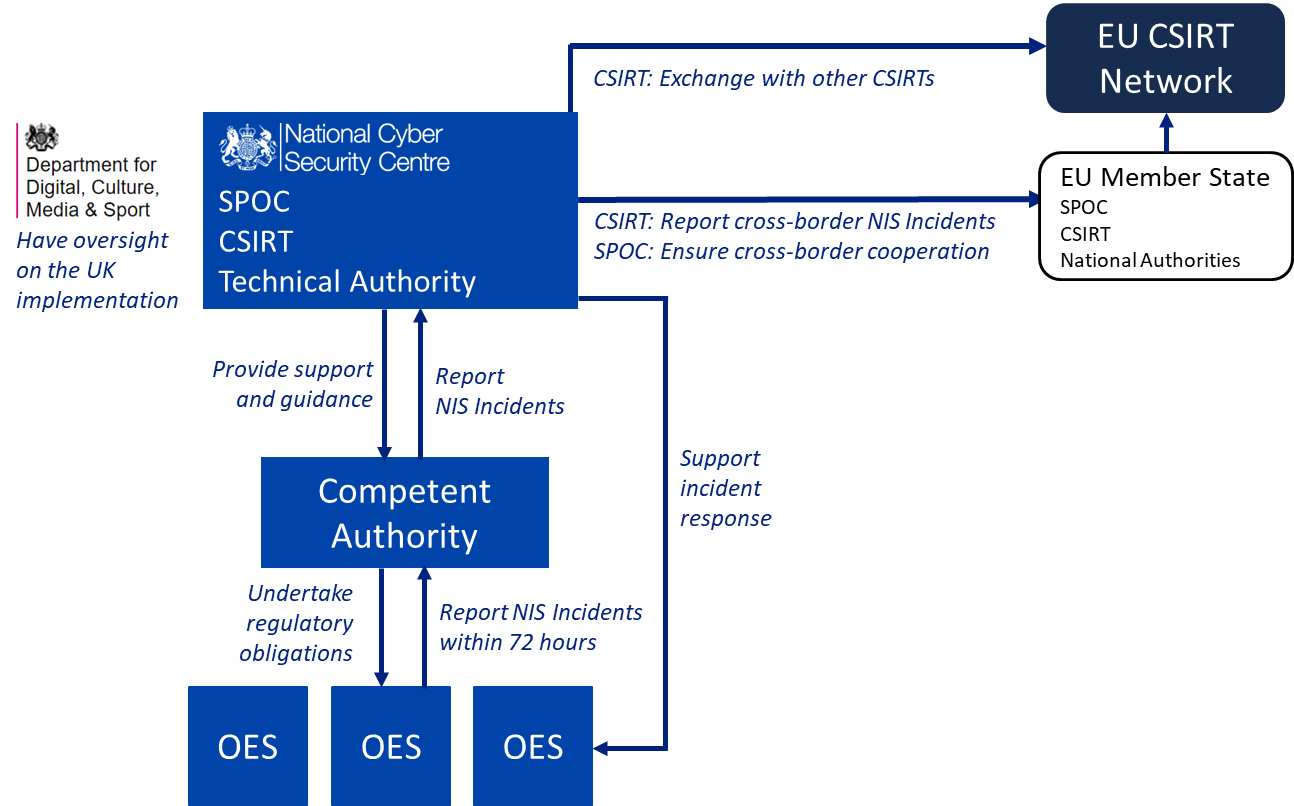
Figure 1. Summary of interactions in the UK (non-exhaustive)
The NIS Regulations for OESs and RDSPs
Obligations of OESs and RDSPs
As we have seen, OESs and RDSPs must comply with the requirement of the NIS Regulations. Yet, it is important to remember that they are not security experts. Hence, security must not be a blocker to their operations. For that purpose, they seek guidance from their Competent Authority and the NCSC.
In that spirit, the NCSC has developed the Cyber Assessment Framework (CAF). The CAF proposes an outcome-based approach to security: it defines security objectives to attain without being prescriptive. OESs can use the CAF to assess and justify the “appropriate and proportionate” nature of their security measures. We will have a deeper look at the CAF in our next article.
For RDSPs, the NIS Regulations requires them to implement security measures to protect five domains:
- The security of their systems and facilities;
- Incident handling;
- Business continuity management;
- Monitoring, auditing and testing;
- Compliance with international standards.
There is currently no equivalent of the CAF for RDSPs. For that purpose, RDSPs current obligations mostly refer to the notification of NIS Incidents to their CA, the ICO.
For both OESs and RDSPs, it is currently very difficult (and not expected) to be fully compliant with the requirements of the NIS Directive. Hence, it is important that they can demonstrate how they consider the requirements of the NIS Regulations and how they have taken actions around them.
Self-assessment [OES Only]
In the UK, OESs must perform a self-assessment of their current posture against the NIS Directive and communicate the results to their CA. The objective of this self-assessment is to collect evidence, assess their existing security posture and identify gaps.
Most CAs require OESs in their sector to perform this self-assessment using the CAF. In the health sector, OESs must use the “Data Security and Protection Toolkit” that NHS Digital developed to cover both the NIS Regulations and the GDPR/Data Protection Act 2018.
Note: At the time of this writing, this approach is not formalised for RDSPs. CAs are currently reviewing the first self-assessments for OESs.
Improvement plan [OES Only]
Following their self-assessment, OESs must develop an improvement plan and communicate it to their CA. This goes with the spirit of the NIS Regulations: CAs do not expect full compliance with the NIS Regulations but they expect OESs to take security seriously and know what to do to improve their current posture.
This improvement plan will rely on the self-assessment and its gaps so that it is realistic and attainable. For instance, some OESs may prioritise security measures that mitigate significant risks, while others may focus on quick-wins that can improve their security posture.
Note: To support this phase, the NCSC and CAs can develop “profiles” that emphasize specific areas of improvement. Again, this approach is not formalised for RDSPs at the time of this writing.
Collaboration with their Competent Authority
The NIS Regulations emphasizes the importance of collaboration and exchange between Competent Authorities and their OESs/RDSPs. The objective is to avoid a tick-boxing approach to security by making it yet another regulatory requirement to comply with.
For that purpose, OESs and RDSPs have all interest to exchange regularly with their CA on their expectations, implementation challenges, etc. They must also notify their CA of NIS Incidents within 72 hours after discovery. They can also notify non-significant incidents as it can serve to improve the overall security posture in a given sector.
OESs and RDSPs must also support their CA in their compliance assessment, by collaborating with them during the scoping part, by identifying relevant stakeholders, by supporting CAs in their inspection, etc.
Note: If an OES is reliant on a RDSP, the OES must notify its Competent Authority (and not the ICO) as soon as the NIS Incident occurs.
Implementation Roadmap [Focus on OES]
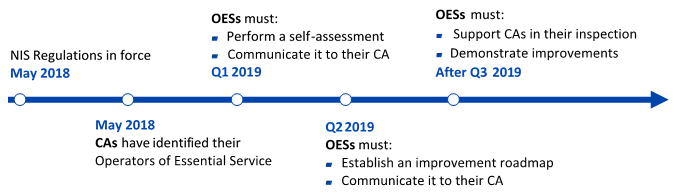
Figure 2. Timeline for the NIS Directive in the UK
The NIS Regulations for CAs
As discussed previously, CAs assess the compliance of their OESs and RDSPs with the NIS Regulations. CAs also have a support role in regard with the implementation of appropriate and proportionate security measures. For that purpose, they can rely on several mechanisms.
Formal notices
The first mechanism is the usage of formal notices. A CA can issue three types of formal notices to an OES/RDSP:
Information notices
Information notices are the first type of notices. CAs can request an OES/RDSP to provide information on their security and all necessary evidence. For example, a CA can issue an information notice to get precision on the self-assessment.
Enforcement notices
Enforcement notices are undertakings: they require an immediate action from OESs/RDSPs. CAs can issue enforcement notices if they believe that an OES/RSDP has failed to comply with regulatory requirements. For example, failure to provide evidence after an information notice
The NIS Regulations requires enforcement to be reasonable and proportionate.
Penalty notices
Penalty notices impose monetary fines in case of a contravention. CAs can issue them if an OES/RDSP fails to take corrective action after an enforcement notice. They must remain rare and may be used in case of severe non-compliance (e.g. failure to remediate major security risks that could cause a NIS Incident).
The NIS Regulations specifies that penalties must be appropriate and proportionate to the breach.
Power of Inspection
The second mechanism is the power of inspection. As a regulator, the CA can decide to inspect an OES/RDSP and assess its efforts to compliance with the NIS Regulations. It is important for CAs and OESs/RDSPs in their sector to follow a collaborative approach to prepare and perform this inspection.
These inspections can serve several purposes that can help OESs with feedbacks, and clarify any questions the CA may have on the appropriate and proportionate nature of the security measures.
Moreover, after performing several inspections in their sector, CAs will gain a better visibility on the overall security level in their sector. They can then communicate on trends, good practices, and eventually adapt the existing process.
The NIS Regulations gives a CA the ability to:
- Conduct an inspection directly;
- Appoint a person to conduct an inspection on its behalf;
- Direct the OES/RDSP to appoint a person who is approved by that authority to conduct an inspection on its behalf.
Note: At the time of this writing, there is no approved list of third-party inspectors.
Enforcement and Penalties
In case of a breach of regulation or repeated infringements (a contravention), a CA can act to enforce the regulation. In the worst-case scenario, a CA can issue penalties.
Enforcement
The spirit of the NIS Regulations is to improve the global security posture. Hence, CAs must consider whether an enforcement is reasonable and proportionate depending on the facts and circumstances of the case.
Additionally, CAs must keep this collaborative approach about enforcement and contravention. For instance, they must consider the steps taken by the OES or RDSP to rectify the contravention, or if a contravention is also liable to enforcement under another enactment (such as the GDPR).
Note: For the first year, it is recommended that CAs take a cautious approach to enforcement
Penalties
A regulation with no penalty has little chances to succeed! For that purpose, the NIS Regulations adopts a very dissuasive penalty regime to make sure that security becomes a priority at board-level!
CAs can issue penalties following the non-respect of an enforcement notice, repeated contraventions, multiple NIS Incidents, etc. Nevertheless, CAs must ensure that a penalty remains appropriate and proportionate to the failure (e.g. it does not create more impact onto service delivery).
The amount imposed in a penalty notice is proportionate to the potential impact on the service, its users and the economy:
- A penalty cannot exceed £1 Million for any contravention which the CA determines could not cause a NIS Incident.
When the CA determines that a material contravention has caused or could cause an incident, the penalty can be as high as:
- £3,4 Millions for a reduction of service provision by the OES or RDSP for a significant period of time.
- £8,5 Millions for a disruption of service provision by the OES or RDSP for a significant period of time.
- £17 Millions for an immediate threat to life or significant adverse impact on the United Kingdom economy.
It is expected that OESs and RDSPs take corrective action before falling into a penalty regime. In any case, they can request a review of the penalty.
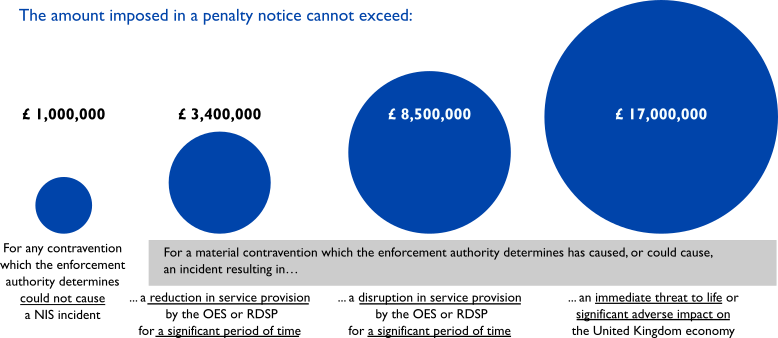
Figure 3. Penalties in the UK
Conclusions
The NIS Regulations is the transposition of the NIS Directive in the UK, which excludes the banking and financial market infrastructure sectors. The NIS Regulations aims to strengthen the overall security posture in the UK. For that purpose, it defines roles and responsibilities according to the existing regulatory environment. It also attributes the NCSC the role of “Technical Authority” to support Competent Authorities on technical matters.
The NIS Regulations remains within the spirit of the NIS Directive as it mandates a collaborative approach between Competent Authorities and their OESs/RDSPs. Most requirements are similar to the NIS Directive. Yet, the NIS Regulations brings some interesting complements:
- It specifies a 72-hour timeframe for OESs and RDSPs to notify NIS Incidents after discovery;
- It gives strong enforcement capabilities to Competent Authorities, with dissuasive penalties.
Moreover, UK OESs must perform a self-assessment and develop an improvement roadmap accordingly. They must communicate their results to their CA which will act upon them.
In the next article, we will talk about the Cyber Assessment Framework.
About cetome
cetome is an independent security consultancy based in London, UK and Lyon, France and operating globally. We work with organisations where security is important and that need to tackle several challenges in terms of resources, capabilities or skills. At cetome, we understand the challenges of the NIS Directive its complexity. We work with OESs to help them assess their security posture and implement appropriate and proportionate security measures. cetome has developed and delivered the only GCHQ Certified Training on the NIS Directive and the Cyber Assessment Framework.
About the Author
Dr. Cédric LÉVY-BENCHETON is the CEO and founder of cetome. Cédric has expertise in the NIS Directive and OT/ICS security. Cédric previously worked at ENISA, the European Union Cyber Security Agency. Before that, Cédric designed critical networks for public transports.
